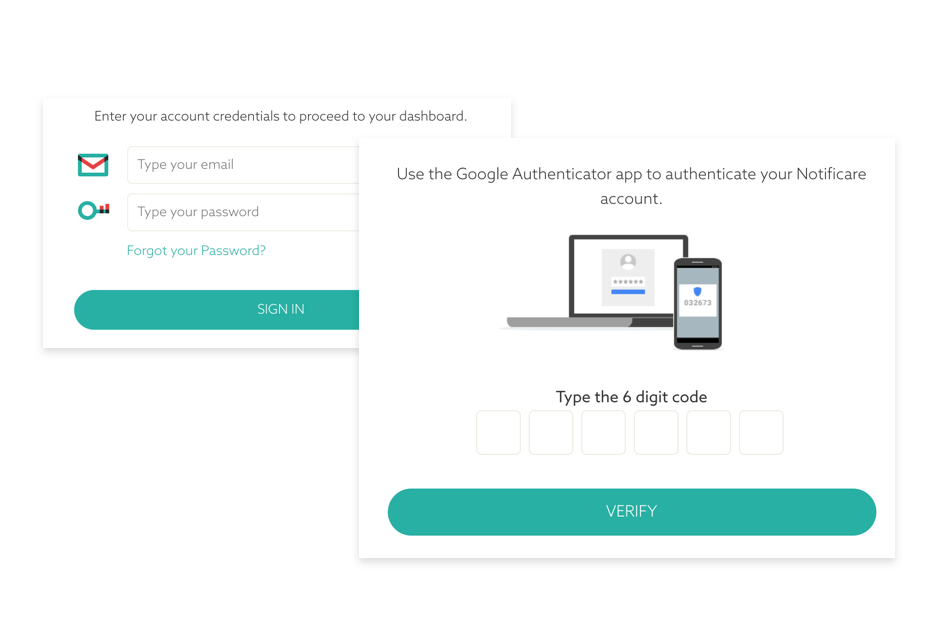
We've taken all the steps necessary to protect your data.
Meet the platform that keeps your customer data safe.
GDPR Compliance
Since we are processing your data and that of your users, we want to make sure those same users can trust you for handling their data with care according to the EU's General Data Protection Regulation.
We’ve removed the complexity involved in enforcing your organization’s data management policies, by automatically discarding data stored in our platform as soon as it reaches your data lifetime thresholds.
We’ve removed the complexity involved in enforcing your organization’s data management policies, by automatically discarding data stored in our platform as soon as it reaches your data lifetime thresholds.